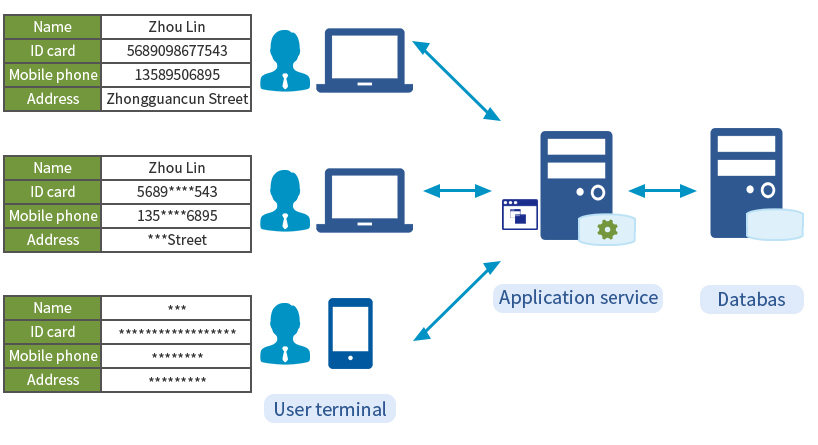
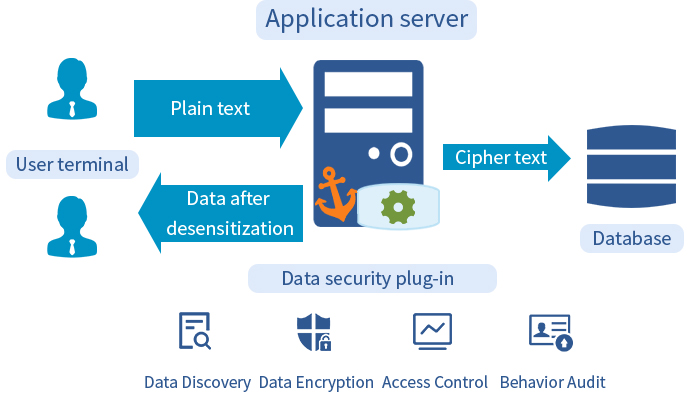
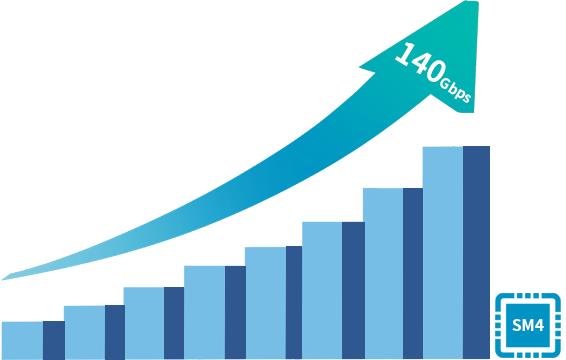
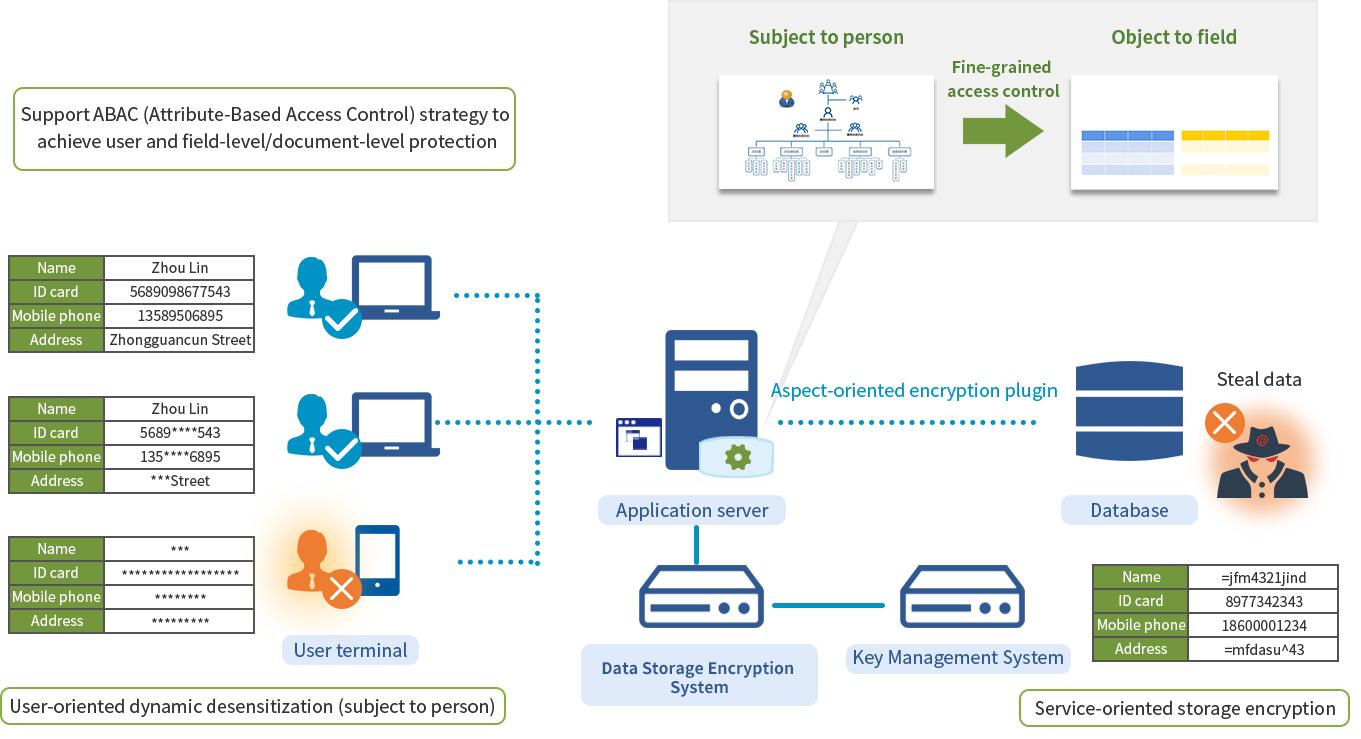
CipherGateway Data Storage Encryption System is a data security cryptographic product which can be deployed agilely, aimed at application system protection. Only configuration-level deployment is required to achieve database storage encryption for any specified field (to prevent internal IT personnel, external hackers, etc.), and by combining with the identity of the logged-in users to achieve dynamic desensitization and auditing(to prevent unauthorized access by internal staff)without any source code of the existing applications being re-coded.
Typical scenarios for the application of products include personal information protection for government and corporate customers, business secret protection for companies, cipher security assessment and rectification for the government, state-owned enterprises, financial and other industries, as well as data protection in military industry and confidential industry, etc. It can be protected against a single application or dozens of applications in batches. It also supports structured data such as sensitive fields and unstructured data such as document files.