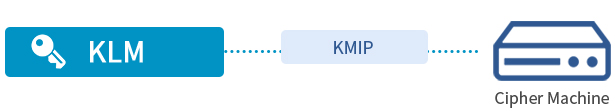
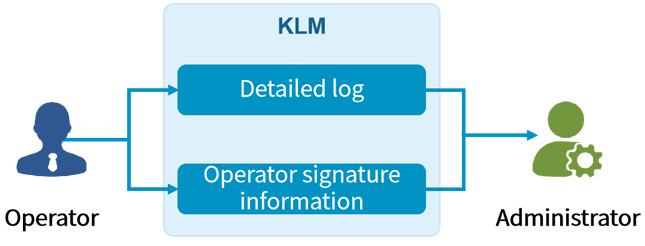
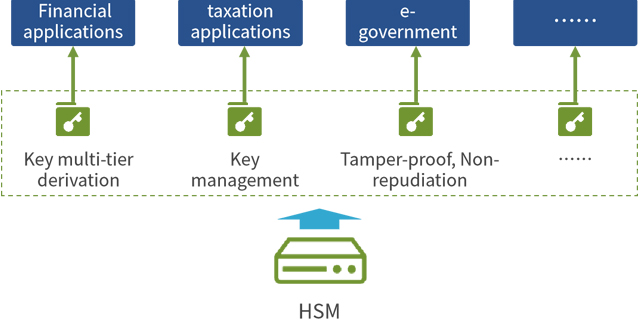
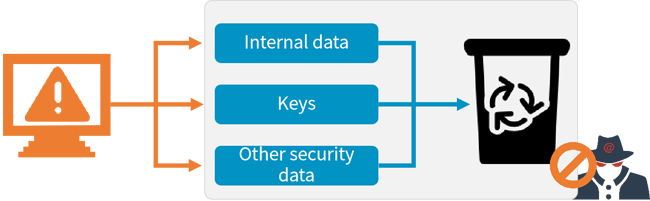
CipherGateway Key Management System (abbreviated as: KLM) provides full life cycle management of keys, including key generation, key storage, key distribution, key backup, key update, key revocation, and key archiving, key recovery and security management, etc.
CipherGateway Key Management System has passed the inspection of the State Cryptography Administration, and follows the requirements of the "Certificate Authentication Key Management System Testing Specification" and the "Cryptographic Device Management Symmetric Key Management Technical Specification" issued by the State Cryptography Administration, and adopts leading technologies. By combining with the authentication system, it can provide technical and strategic security guarantees for PKI application field.